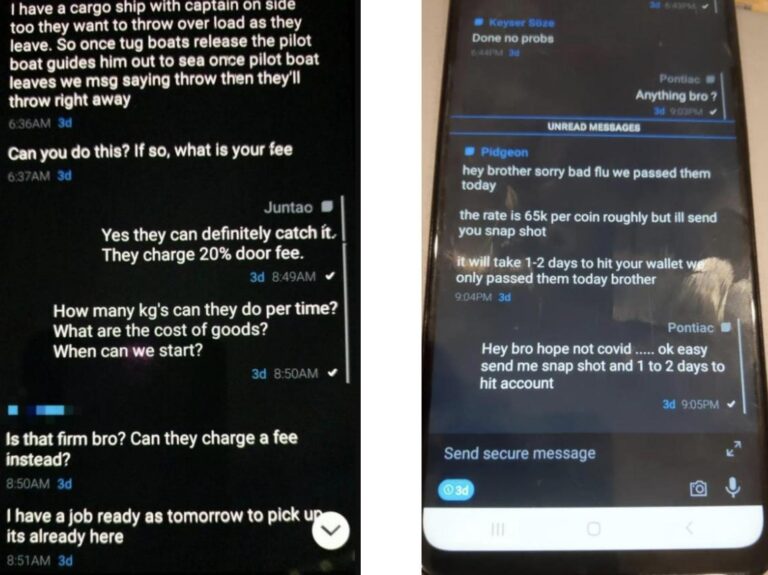
In a landmark development for law enforcement, the first individual has been sentenced in connection with the San Diego FBIŌĆÖs high-profile encrypted phone sting that infiltrated criminal networks around the globe. The operation, which targeted encrypted communications used by criminals to evade detection, has been hailed as a significant breakthrough in combating organized crime and illicit activities. This sentencing marks a critical milestone in the ongoing efforts to leverage advanced technology in the fight against transnational crime, underscoring the FBIŌĆÖs capability to penetrate secure channels once thought impenetrable.
First Person Sentenced in San Diego FBI Encrypted Phone Sting Exposes Global Criminal Networks
In a landmark case, the San Diego FBI has successfully concluded its covert operation infiltrating encrypted communications used by global criminal enterprises. The individual sentenced is the first to be held accountable following the FBI’s unprecedented phone sting that targeted illicit networks operating in multiple continents. This breakthrough showcases the bureau’s advanced capabilities in cyber surveillance and international law enforcement collaboration, dismantling extensive drug trafficking, money laundering, and arms smuggling rings.
Key aspects of the operation:
- Deployment of specialized encrypted devices embedded with FBI surveillance technology
- Monitoring and intercepting encrypted messages of high-profile criminal figures
- Real-time intelligence that enabled swift arrests across borders
- Collaboration with global law enforcement agencies to amplify impact
| Category | Impact | Outcome |
|---|---|---|
| Drug Trafficking | 80% Operation Coverage | Multiple High-Value Busts |
| Money Laundering | Millions Recovered | Financial Disruptions |
| Weapons Smuggling | Weapons Seized | Reduced Armed Crime |
Authorities emphasize that this sentencing marks only the beginning of a larger effort to eradicate organized crime’s reliance on encrypted digital communications. With the technology and legal frameworks now in place, more defendants connected to these transnational networks are expected to face charges imminently.
Operation’s Impact on International Crime and Law Enforcement Collaboration
The recent sentencing marks a pivotal moment in international efforts to dismantle encrypted communication networks exploited by criminals. This operation’s success has reverberated across borders, facilitating unprecedented levels of cooperation between law enforcement agencies worldwide. By penetrating encrypted platforms, agencies gained critical intelligence that led to multiple arrests and disrupted organized crime syndicates spanning continents. The collaborative framework established illustrates a new paradigm where information sharing and synchronized actions dramatically enhance the global fight against cyber-enabled crime.
Key aspects of this international law enforcement synergy include:
- Real-time intelligence exchange enabling swift action against high-profile targets.
- Joint task forces that overcome jurisdictional challenges and legal barriers.
- Enhanced surveillance capabilities through shared technology and expert training.
| Agency | Role | Impact |
|---|---|---|
| FBI San Diego | Lead Operation | Primary intelligence collector and coordinator |
| Europol | Support & Analysis | Cross-border crime linkage and data analytics |
| Australian Federal Police | Field Enforcement | Arrests and local surveillance |
| Interpol | Global Coordination | Facilitated international legal assistance |
Legal Precedents Set by FBI’s Use of Encrypted Phone Surveillance
The FBIŌĆÖs covert operation involving encrypted phone surveillance has established significant legal benchmarks, reshaping the landscape of digital privacy and law enforcement overreach. This initiative marked a pivotal moment where government agencies successfully intercepted and decrypted communications on a massive scale, challenging prior assumptions about the reach of encrypted technologies. The courts have now grappled with balancing constitutional protections against the imperative to dismantle sophisticated criminal networks exploiting encrypted channels.
Key legal precedents include:
- Affirmation of warrant validity: Courts upheld the FBIŌĆÖs use of warrants to access encrypted data, marking a critical endorsement of evolving investigative techniques in cybercrime cases.
- Clarification of privacy limits: Judges delineated the scope of Fourth Amendment protections concerning digital data, highlighting scenarios where surveillance tools may justifiably bypass encryption safeguards.
- Standards for future surveillance: Established guidelines for monitoring encrypted communications without undermining broader privacy rights, setting a roadmap for law enforcement agencies worldwide.
| Legal Aspect | Impact | Judicial Outcome |
|---|---|---|
| Encrypted Data Access | Broad law enforcement tools | Warrants deemed Constitutional |
| Privacy Protection | Defined limits on surveillance | Balanced rights with security |
| Surveillance Protocols | Uniform standards set | Framework for future cases |
Recommendations for Strengthening Digital Security and Privacy Measures
As encrypted communication continues to be a double-edged swordŌĆöproviding privacy for law-abiding citizens while enabling illicit activitiesŌĆöit is imperative for both governments and tech companies to adopt balanced approaches that protect security without compromising individual rights. Implementing multi-layered encryption standards that are resistant to unauthorized breaches yet allow lawful interception under strict judicial oversight can help strengthen digital security frameworks.
- Establish clear protocols: Define transparent methods for lawful access with accountability measures to prevent abuse.
- Enhance public-private collaboration: Foster partnerships between law enforcement agencies and technology providers to develop secure, privacy-compliant tools.
- Invest in cybersecurity education: Equip users and developers with knowledge about privacy best practices and potential vulnerabilities.
- Promote regular audits: Conduct independent assessments of encryption solutions to identify weaknesses before malicious actors exploit them.
| Action | Benefit | Stakeholders |
|---|---|---|
| Multi-layered Encryption | Enhanced data protection | Developers, Users |
| Judicial Oversight | Prevents misuse & abuse | Government, Judiciary |
| Education Initiatives | Increased awareness | Educators, Public |
| Public-Private Partnerships | Balanced privacy & security | Law Enforcement, Tech Firms |
To Conclude
The sentencing of the first individual caught in the San Diego FBIŌĆÖs encrypted phone sting marks a significant milestone in the agencyŌĆÖs global crackdown on organized crime. By infiltrating secure communications once thought impenetrable, law enforcement has exposed a new frontier in cyber investigations and criminal surveillance. As this case sets a precedent, authorities continue to refine their tactics in the ongoing battle against illicit networks operating under the cover of digital privacy. The full impact of this operation will likely unfold in the coming months, as further prosecutions and intelligence breakthroughs are expected to follow.